The Liberation Tigers of Tamil Eelam’s (LTTE) Intelligence Wing, Tiger Organization Security Intelligence Service (TOSIS)
The author would like to dedicate this article to Colonel Tuan Nizam Muthaliff RWP, MI (July 12, 1966 – May 31, 2005) was the former Commanding Officer of the 1st Battalion Military Intelligence Corps, Directorate of Military Intelligence (DMI) of Sri Lanka, whose perseverance and courage in the face of adversity has served as an inspiration – Kagusthan Ariaratnam.
எப்பொருள் யார்வாய்க் கேட்பினும் அப்பொருள் மெய்ப்பொருள் காண்பது அறிவு.
– திருக்குறள், அதிகாரம் 43, குறள் 423
Whatever the Matter is being Told, Whoever the Person is Telling, Discern the Truth is Wisdom.
Fall 2015
Unclassified
Introduction
Secret operations are essential in war, upon them the army relies to make its every move. … An army without secret agents is exactly like a man without eyes or ears.
Many have said that to fight a war, the most basic and essential asset is that of a secret service or organization exceptionally dedicated to intelligence-gathering operations. It may be a government agency, the military, or the police. This is also relevant to a non-state actor or a terrorist group.
The Liberation Tigers of Tamil Eelam (LTTE), a guerrilla-cum-terrorist organization fighting to establish a separate homeland for the minority Tamil population in Sri Lanka, staged about 250 suicide operations from July 1987 until today. All these have been within Sri Lanka, except for the assassination of former Indian Prime Minister Rajiv Gandhi by Thenmozhi Rajaratnam, alias Dhanu, on May 21, 1991. With a few exceptions, the LTTE claimed responsibility only for the suicide attack operations it conducted against military targets in Sri Lanka’s northeastern region. The organization refrained from claiming responsibility for operations against VIP and non-military infrastructure targets since all such missions and/or operations were carried out by its Intelligence Wing. Attributable to this Intelligence Wing’s operations is the LTTE’s labeling as a “terrorist outfit” rather than a “liberation movement” by the USA, Canada, the EU, and India.

The LTTE was one of the most innovative rebels, who ran a de facto state with an army, rudimentary navy and air force, intelligence wing, suicide bombers, police, courts, tariffs systems, gold coin currency system, and banks. Many other terrorist organizations, including al Qaeda, Taliban, Hamas, and Daesh, have used LTTE’s modus operandi and its tactics as a “template” for terrorism. In May 2009, the Sri Lankan security forces militarily obliterated the LTTE; nonetheless, an unknown number of LTTE remnants have dispersed into countries as far as Australia and Canada. Thus, the LTTE is a defunct fighting organization within Sri Lanka; however, they are very much alive globally as a quasi-socio-political organization led by its intelligence wing, Tiger Organization Security Intelligence Service (TOSIS). Therefore, the LTTE threatens not only the domestic stability of Sri Lanka but also, by its example, the security of the regional and global systems as it has been waging “hybrid warfare” in the international arena.
Even though the Terms of Engagements and/or the Rules of Engagements differ from a conventional force, a terrorist network’s secret missions and/or operations are still conducted in a well-organized and professional manner nowadays. As this author had no choice but to work for the Intelligence Wing of the LTTE, he experienced how a terrorist “cell” is structured and operates. This author’s understanding is that they were not well structured. Still, after incurring heavy losses of their sources, such as agents and informants identified and arrested by the Sri Lankan security forces, the LTTE organization realized it should establish a professional intelligence unit.
Since they didn’t have the resources a government intelligence agency would have, they primarily relied on Human Intelligence rather than more sophisticated Signal Intelligence, Electronic Intelligence, Imagery Intelligence, Technical Intelligence, etc. To train their cadres, the organization acquired books, magazines, films/movies, and training manuals from foreign countries to learn about the world’s famous intelligence agencies such as the Gestapo of Germany, the KGB of the Soviet Union, the CIA of America, MI5 and MI6 of Britain, the SDECE/DGSE of France, Savak and Vevak of Iran, Mossad and Shin Bet of Israel, RAW of India and ISI of Pakistan. For instance, LTTE’s Intelligence Wing acquired an original copy of the training manuals belonging to Inter Service Intelligence (ISI), the Pakistani internal and external intelligence agency.
They also brought in mercenaries to train their most senior cadres with the necessary linguistic skills; later, those senior cadres trained the rest of the Intelligence Wing cadres in the organization.

The LTTE’s Intelligence Dominance
In the region of the Indian subcontinent, LTTE had the dubious distinction of having been a sort of pioneer in terrorism. Some of its ground-breaking achievements were the suicide vest/belt, suicide vehicle bombing, and the elimination of leaders using suicide commando raids, all of which the Taliban and al-Qaeda have imitated. The think-tank behind all these terrorist groups’ operations, including the LTTE’s, was the Pakistan military-backed Inter-Service Intelligence (ISI). As an insider of the LTTE’s Intelligence Wing, this author is well aware that after the assassination of Rajiv Gandhi by the LTTE, the ISI cunningly exploited the opportunity to use LTTE to systematically destabilize India from the South where its strategic hard targets are located. Since then, the ISI began covertly aiding the LTTE with intelligence training and tactics. For instance, most of the intelligence tradecraft training this author underwent in 1993, including intelligence gathering, intelligence analysis, and agent recruitment, handling, and exploitation with Mathavan Master of the LTTE Intelligence Wing, was based on the original ISI agent handling and exploitation model.
In May 1993, following the assassination of Sri Lankan President Ranasinghe Premadasa, was led and handled by Janan Master of the LTTE Intelligence Wing, the leader of the movement, Velupillai Prabhakaran, and Pottu Amman, the head of TOSIS, decided to send Janan Master to Tamil Nadu to act as a liaison between the LTTE Intelligence Wing’s “political activities and liaison division” and the pro-LTTE political party leaders in Tamil Nadu, such as V.Gopalaswamy, President of the Marumalardchi Dravida Munnetra Kazhakam (MDMK), Dr. S. Ramadoss, the founder-leader of Pattali Makkal Katchi (PMK), Pazha Nedumaaran, President of the Tamil Nationalist Movement (TMM), K. Veeramani, President of Dravidar Kazhagam (DK), and Thol. Thirumavalavan, President of the Viduthalai Chiruthaigal Kadchchi (VCK). Prabhakaran wanted to understand the mindset of the Tamil Nadu politicians towards his organization and had hoped to ignite the Tamil nationalism induced by the politicians by placing a high-level LTTE liaison in their midst.
There was also another reason behind sending Janan Master to Tamil Nadu. In the aftermath of the assassination of Rajiv Gandhi, India’s external intelligence agency, the Research and Analysis Wing (RAW), waged a massive covert operation against LTTE. However, due to LTTE’s excellent counterintelligence unit led by Kapil Amman and including Janan Master, this mission was a huge disaster and embarrassment for India. The LTTE mounted surveillance on all of RAW’s rings inside their controlled area, arrested all the agents, spies, and cadres who were involved, and eventually dismantled the entire operation.
The LTTE as a template for terrorism
In 1995, when this author was an LTTE Intelligence Wing cadre, he was provided with a videotape by Prabhakaran’s military adviser, Thinesh Master. He was asked to identify what type of aircraft had been shot down by an LTTE missile so that they could provide the technical details of the particular aircraft to the LTTE-controlled newspapers. On the tape, this author saw a few men with long beards and wearing turbans giving demonstrations to LTTE cadres in the Jaffna peninsula on how to shoot down the Avro HS-748 transport aircraft with shoulder-fired surface-to-air Stinger missiles. This author was curious and questioned Thinesh Master about who the men were. The latter replied that they were Afghan Mujahedeen.
According to Sri Lanka’s Ministry of Defence (2008), intelligence experts have long suspected the existence of connections between the LTTE and other internationally designated terrorist organizations, including al-Qaeda and the Taliban. These connections came under more detailed scrutiny due to the 9/11 attacks.
Some of the incidents cited to prove these suspicions include:
The similarities between previous LTTE attacks against Sri Lanka Navy ships and the al-Qaeda attack on the USS Cole which killed 17 US Navy sailors.
Evidence that the LTTE provided forged passports to Ramzi Yousef, the man who carried out the first attack against the World Trade Center in New York in 1993.
The smuggling of weapons by the LTTE from Islamics in Pakistan to their counterparts in the Philippines.
Allegations that the LTTE stole Norwegian passports and sold them to the al-Qaeda organization to earn money to fund their arms purchases.
Increasing intelligence reports that the LTTE was smuggling arms to various terrorist organizations using their covert smuggling networks, and findings by the London-based International Institute for Strategic Studies that they were building commercial links with al-Qaeda and other militants in Afghanistan.
(Ministry of Defence, Sri Lanka, 2008)
Other security experts, including Glen Jenvey, have also claimed that al-Qaeda has copied most of its terror tactics from the LTTE. He highlighted the LTTE as the mastermind that sets the pattern for organizations like al-Qaeda to pursue. Some of the comparisons he used to draw his conclusions are:
The LTTE invented the modern suicide bomber and deployed it against political, military, and civilian targets. Islamic groups copied the LTTE by carrying out similar suicide attacks.
The LTTE attack on the World Trade Centre in Sri Lanka was followed by attacks by al-Qaeda on the World Trade Center in New York.
The LTTE’s use of a women’s section has been copied by al-Qaeda and Chechen terrorists, for example, the “Black Widows” who played a role in the Moscow theater hostage crisis and have carried out suicide bombings.
Attacks on civilians in buses and trains in Sri Lanka are similar to the al-Qaeda attacks on public civilian transport during the July 2005 bombings in London.
(Ministry of Defence, Sri Lanka, 2008)
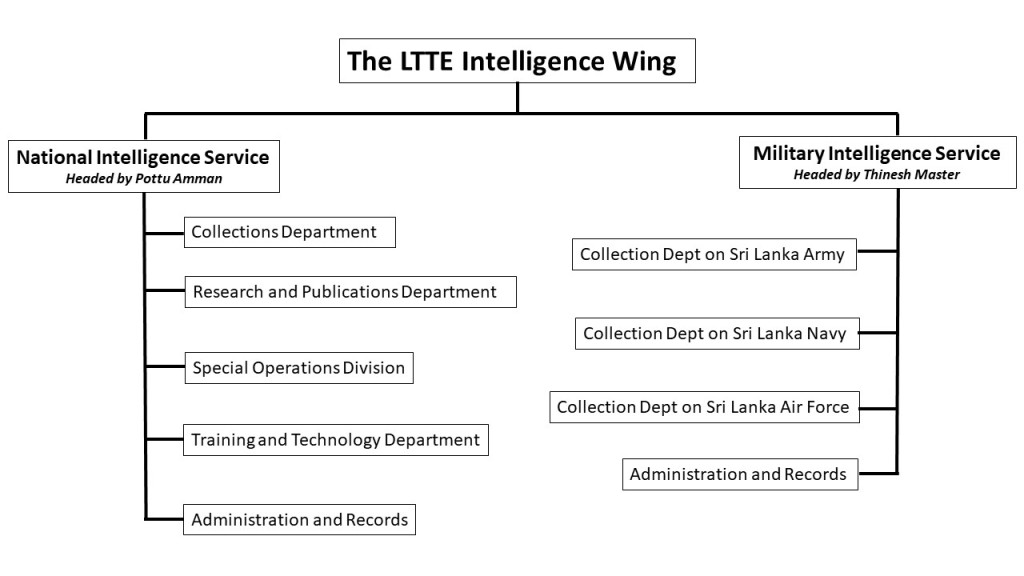
In this context, it is vital to analyze the LTTE’s Intelligence Wing, also known as “Tiger Organization Security Intelligence Service” (TOSIS), in detail. The TOSIS was reportedly founded at the end of the 1980s when the LTTE was fighting with the Indian Peace Keeping Force (IPKF). It functioned as the primary intelligence service of the LTTE until 1993, when it was divided into two sub-units, the “National Intelligence Service” and the “Military Intelligence Service.” The latter did not have cadres on the ground in hostile areas, but it had agents in the Sri Lankan security forces. The presence of a second intelligence service gave the LTTE the advantage of cross-checking and verifying both raw data and assessments.

National Intelligence Service ( Thesiya Pulanaivu Pirivu) Headed by Pottu Amman
Although the LTTE was trained by India’s RAW in the early 1980s, the LTTE’s National Intelligence Service’s strategic operating structure and tactics were more similar to the Mossad of the 1980s, except for its agent handling model. From the outset, the LTTE’s intelligence wings imitated the Israeli Mossad’s own Sayanim system, the use of non-stipend but activatable sympathizers to provide one-off assistance when needed, which were designated Kalam and Pulam in the case of Tamils residing in Sri Lanka or the diaspora, respectively. All in all, the National Intelligence Service had up to 1,500 Kalam and Pulam personnel altogether. Furthermore, Mossad’s operating language is Hebrew, and one of the reasons LTTE’s Intelligence Wing is successful is that it functions entirely in Tamil. The LTTE-Mossad nexus was further corroborated when ex-Mossad officer Victor Ostrovsky’s book “By Way of Deception” was published in September 1990.
There are 5 known departments of the National Intelligence Service:
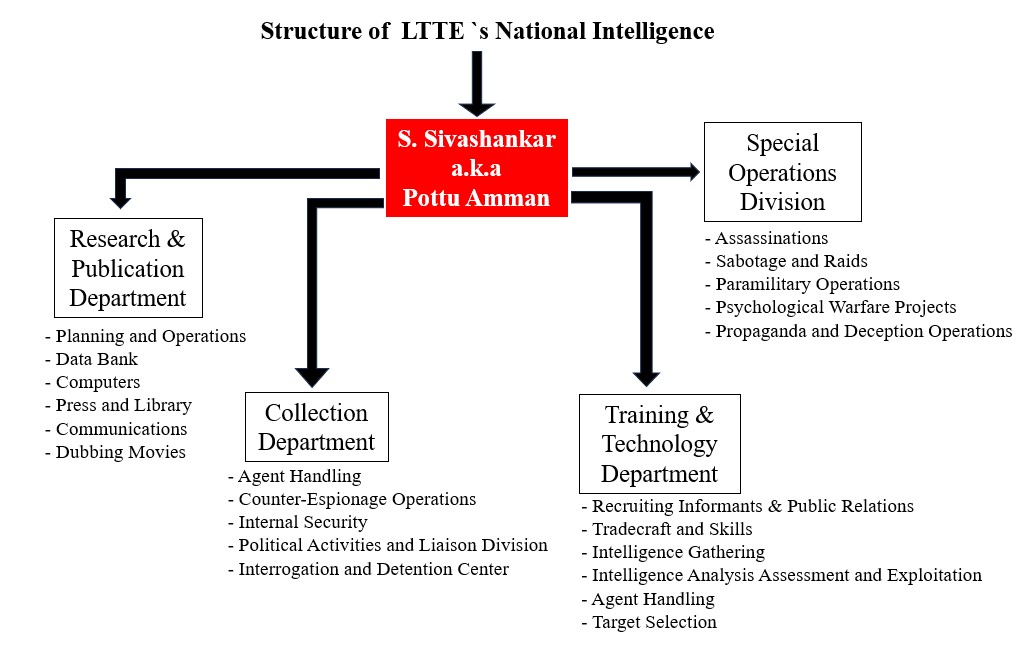
(i) Collections Department: (Thakaval Sekatippu Pirivu) headed by the deputy Kapil Amman. This was the largest Department, with agent handling and espionage operations responsibilities and sub-divisions in the northern, eastern, and southern parts of Sri Lanka. This body also coordinated with the LTTE’s police force in the areas they controlled. The Department consisted of several desks that were responsible for specific areas, such as,
- Agent Handling
- Counter-Espionage Operations
- Internal Security
- Political Activities and Liaison Division
- Interrogation and Detention Center
(ii) Research and Publications Department: (Aaivu Mattrum Veliyeeddu Pirivu) is headed by Mathavan Master and is responsible for intelligence production, including daily situation reports, weekly summaries, and detailed monthly reports. This Department was organized into several categorically specialized sections, such as,
- Planning and Operations
- Data-Bank
- Computers
- Press and Library
- Communications
- Dubbing Movies
(iii) Special Operations Division: (Ellalan Padai) headed by Janan Master, also the Principal Agent Handler of the LTTE Intelligence Wing. The “Black Tigers” – a highly secretive suicide squadron – were also attached to this division under the direct command of the LTTE leader. This covert squadron conducted susceptible operations such as
- Assassinations
- Sabotage and Raids
- Paramilitary Operations
- Psychological Warfare Projects
- Propaganda and Deception Operations
(iv) Training and Technology Department: (Payitchi Mattrum Tholilnudpa Pirivu), also headed by Mathavan Master, responsible for the training and development of advanced technologies for support of both National and Military intelligence, including the suicide vest/belt, modifying weapons and explosive-filled vehicles, spy tools, etc.
(v) Administration and Records: (Nirvaakam Mattrum Arikkai Pirivu) headed by Sankar. This body mainly focused on administration, personnel, finance, logistics, and welfare.

Military Intelligence Service, (Iranuva Pulanaivu Pirivu) Headed by Thinesh Master
The Military Intelligence Service of LTTE was formed in 1993, almost 10 years after the LTTE had established its primary National Intelligence Service, to keep military-related operations compartmentalized. There was a “Long-Range Reconnaissance Patrol” (LRRP) team operating under the LTTE’s military wing, known as Viseda Vevu Pitivu, that played a crucial role in assassinating Sri Lankan Army General Denzil Kobbekaduwa and ten other high-rank army officers with him. LRRP cadres infiltrated and laid an anti-tank mine in a military complex in the island’s northern part. The Viseda Vevu Pitivu (LRRP) was the brainchild of Thinesh Master. He was thus praised for the victory and then appointed the head of the newly formed Military Intelligence Service.
The Military Intelligence Service was relatively small and operated on a lower scale than the National Intelligence Service. It only focused on gathering intelligence on Sri Lankan security forces. Even though the operations were highly compartmentalized, the Military Intelligence Service nonetheless relied on the National Intelligence Service for its training and advanced technologies.
There were 4 known departments of the Military Intelligence Service:
(i) Collections Department on Sri Lanka Army: (Iranuva Thakaval Sekarippu Pirivu) Headed by Kowthaman.
This body exclusively gathered intelligence on Sri Lankan Army bases, artillery units, armored core, heavy weapons, infantry vehicles, and high-ranking officers and their families. They studied in detail the entire Army’s Order of Battle (ORBAT) structure, knowing each division and divisional commander, each brigade and brigade commander, and each regiment and regimental commander up to the company, platoon, and section level officers and then locating where they had been deployed in real-time.
This detailed intelligence gathering helped them to know the exact strength of each army base located anywhere in the country. For instance, LTTE had been gathering intelligence on a northern army complex called “Pooneryn Military Complex” for almost two years before they successfully raided the complex in November 1993. They monitored army communication transmissions and sent their LRRP team to infiltrate and gather real-time intelligence. Then, they made an exact model of the complex and knew the precise strength of the army, each officer’s name, and the location of the artilleries and the armored vehicles. A model was made of the driving compartment of the Czech-made T55 main battle tank that the Sri Lankan Army had in that base; two were eventually seized.
(ii) Collections Department on Sri Lanka Navy: (Kadatpadai Thakaval Sekarippu Pirivu)
Responsible for gathering intelligence on Sri Lankan naval bases, harbors, naval vessels, and personnel. Since LTTE operated from an island, it depended mainly on the sophisticated amphibious group known as the “Sea Tigers” for logistic support. Their duty was to sea control and/or sea denial of the north and east territorial waters of Sri Lanka and to support the unique “Exclusive Economic Zone Marine Logistics Support Team” (EEZ-MLST) of the Sea Tigers.
Therefore, this body coordinated with the Sea Tigers to gather intelligence on the SL Naval bases and vessels. It also collaborated with the unique “Underwater Demolition Teams” (UDT) of the Sea Tigers, who infiltrated the harbors and gathered maritime intelligence. On the other hand, acquiring “Jane’s Naval Fighting Ships” catalog made it easy to build models of every class of the Sri Lanka Navy fighting ships/gunboats. The EEZ-MLST’s sophisticated maritime surveillance radar systems, Global Positioning Systems (GPS), and the dual-purpose special binoculars known as the “Steiner” helped to keep surveillance on daily naval patrolling.

The LTTE leader Velupillai Prabhakaran with Air Tiger pilots before their mission to attack the Palaali military complex
A Black Sea Tiger suicide attack craft 
Air Tiger pilots on a Czech-designed Zlin-143 training aircraft 
Sea Tiger Parade in Jaffna
(iii) Collections Department on Sri Lanka Air Force: (Vaanpadai Thakaval Sekarippu Pirivu)
Responsible for gathering intelligence on Sri Lankan Air Force bases, aircraft, helicopters, and personnel. To simplify the task, this body coordinated with the LRRP team and the unique “Air Tigers” of the LTTE. The LRRP team infiltrated and gathered intelligence on the Air Force bases, runways, signal stations, hangers, oil storages, and personnel. Afterward, contemporary intelligence was used to make models of the Air Force bases. Meanwhile, by gathering data from “Jane’s Fighter Planes,” this body worked with the “Air Tigers” unit to make models of Air Force fighter planes and helicopters.
The final intelligence products were given to the decision-makers who planned, prepared, and executed surprise raids using highly-trained suicide commando units.
(iv) Administration and Records: (Nirvaakam Mattrum Arikkai Pirivu)
As in the National Intelligence Service, this sub-division mainly focused on the Military Intelligence Service’s administration, personnel, finance, logistics, and welfare.
The LTTE Intelligence Training Centre (Pulanaivu Payitchi Maiyam) is known as Spy Tiger Academy.
Headed by Mathavan Master.
I have a high regard for the LTTE for its discipline, dedication, determination, motivation and technical expertise… I was left with the impression that the LTTE was the expression of popular Tamil sentiment and could not be destroyed, so long as that sentiment remained.
– Lieutenant General S.C. Sardesh Pande, IPKF Divisional Commander, Jaffna, in his book “Assignment Jaffna.”

- Recruiting Informants and Public Relations
- Tradecraft and Skills
- Intelligence Gathering
- Intelligence Analysis, Assessment, and Exploitation
- Agent Handling
- Target Selection
(1) Recruiting Informants & Public Relations
As intelligence gathering is, by its very nature, a difficult task of utmost importance, the organization was extremely cautious when recruiting its agents and informants. Most of the time, they tended to cultivate personnel from the same ethnic nationalist group as themselves, who also had the potential to access enemy targets. Great emphasis was therefore placed on public relations among their own people. They necessarily went through an extensive background check of all the individuals they hired, in the process focusing on the individual’s profile, character, vulnerabilities, and motivation to assess if he/she was the right person for the job as well as on the factors that made that particular person want to work for them.
An inadequate administration, poor management, discrimination, ignorance, and oppression by a government sometimes can drive its own people to support a terrorist organization. This makes the organization’s job easier as they can use this opportunity to hire more informants and agents from within the target group. For instance, a few political parties representing minority groups in southern Sri Lanka were continuously discriminated against and ignored by successive ruling parties. This neglect ensured the LTTE’s success when it invited the leaders of these political parties (Vasudeva Nanayakkara and Aarumugam Thondaman), who were then Members of the Sri Lankan Parliament and indoctrinated to work for LTTE’s Intelligence Service as long-term resident agents.
(2) Tradecraft and Skills
Recruits had to undergo a particular training period to acquire the skills to perform their tasks and to learn specific techniques in the espionage trade. This is called Tradecraft and could include such specialties as Agent Handling, Covert Communication, Counter-Interrogation, Reconnaissance, Coding and Decoding, Drawing Maps, Photography, Martial Arts, Linguistic Skills, Driving Skills, Swimming Skills, and so on, depending on the task the agents/informants were assigned to.
Today, intelligence gathering and processing systems allow us to collect and produce intelligence promptly, more rapidly, and accurately than ever. From human sources to satellites, ultramodern aircraft, electronic systems, cameras, imaging, and electromagnetic devices, we can now utilize modern Tradecraft and gather intelligence on a scale and level of sophistication that was unheard of in the past.
While traditional spy agencies employed numerous tradecrafts, including hiding a tracking device onto a briefcase and breaking into the high rise building and offices of an embassy to search through file cabinets while posing as a socialite at a party, terrorist organizations, on the other hand, train their operatives more of practical and unconventional tradecraft techniques such as barbers, cobblers, tailors, and butchers. Once recruits underwent specific tradecraft training, the handlers assessed each recruit, keeping the individual’s potential and background in mind, to confirm whether they were fit to be an agent. This tradecraft training program for terrorists further reinforces their emphasis on HUMINT collection methods.
(3) Intelligence Gathering
Before spies and informants were assigned to a mission, they were instructed in every detail of the target. The target could be a harbor, airport, refinery, warship, aircraft, or even a VIP – whatever it might be, the handlers would brief everything they knew about it in detail and then debrief for the information they needed. Informants had to learn about the specific physical environment in detail beforehand to quickly provide updates on selected targets. To make this task more accessible, the organization preferred to hire government employees working in the area, selecting them carefully after identifying and confirming their potential usefulness.
For instance, the LTTE Intelligence Wing hired a retired government employee who worked as a panelboard controller in Sri Lanka’s largest refinery. They first assigned him to teach a group of Intelligence Wing cadres everything about a refinery, from crude oil tanks to petrol tanks – refining, storing, and distributing petrol, and then the refinery structure. Later, they asked him to visit Colombo, where he had colleagues and friends still working in the same refinery. While visiting his friends at the refinery, he collected the plans of the buildings, maps, the latest technological developments, security measures, storage tanks, and their locations. He was just asked to mail in the information.
Similarly, LTTE Intelligence hired an informant working as a leading aircraftman at China Bay Air Force Base in Trincomalee. He had been visiting his family, living in LTTE’s controlled area, and was forced to work for its Intelligence Wing. Since then, whenever he was seen, he was asked to provide the latest developments, security measures, and maps for the Air Force Base.
While the LTTE gathered intelligence on Colombo Harbour, they hired an engineering student studying Marine Engineering on a scholarship at Mahapola Institute, part of the Colombo Port Authority. As he was a student from a poor family, it was straightforward to motivate him by monetary means. As he had access to the entire container terminal and mechanisms, he was able to provide the latest developments, maps, locations, and security measures.
(4) Intelligence Analysis, Assessment, and Exploitation
After gathering all the required intelligence, it was centralized in the Data Bank, managed by the Principal-Agent Handler (PAH). The PAH received thousands of situational briefing reports daily from various sources. These sources included Intelligence Wing cadres (spies – HUMINT) who operated from all parts of the country, government employees (informants – HUMINT) across the country, military communication and transmission monitoring teams (SIGINT), special reconnaissance teams (LRRP – HUMINT), FDL border patrolling (HUMINT) and open-source intelligence (OSINT). All these sources reported back to the PAH, responsible for managing the Data Bank.
The PAH and his team consisted of an Agent Handler, a Deputy Agent Handler, and more than a dozen Principal Agents. All these agents worked together on analyzing, assessing, and exploiting the intelligence they gathered. They submitted the final intelligence product to the decision-makers to take full advantage of any information that had come to hand for tactical, operational, or strategic purposes. Whether the decision makers took any action, the Principal Agent Handler and his staff always did an assessment weekly to facilitate the Data Bank by conducting systematic intelligence fusion.
(5) Agent Handling
The most successful part of intelligence gathering depends on the security and covert communication an organization provides to its sources. As without security, there’s no intelligence, it is of utmost importance that an organization protect its human assets. This can only be done if there is a systematic way for intelligence to flow from hostile areas to the organization’s data bank. The Principal Agent Handler also ensured his sources were safe and secure. See the following diagram for a visual representation of the structure of the terrorists` agent handling model.
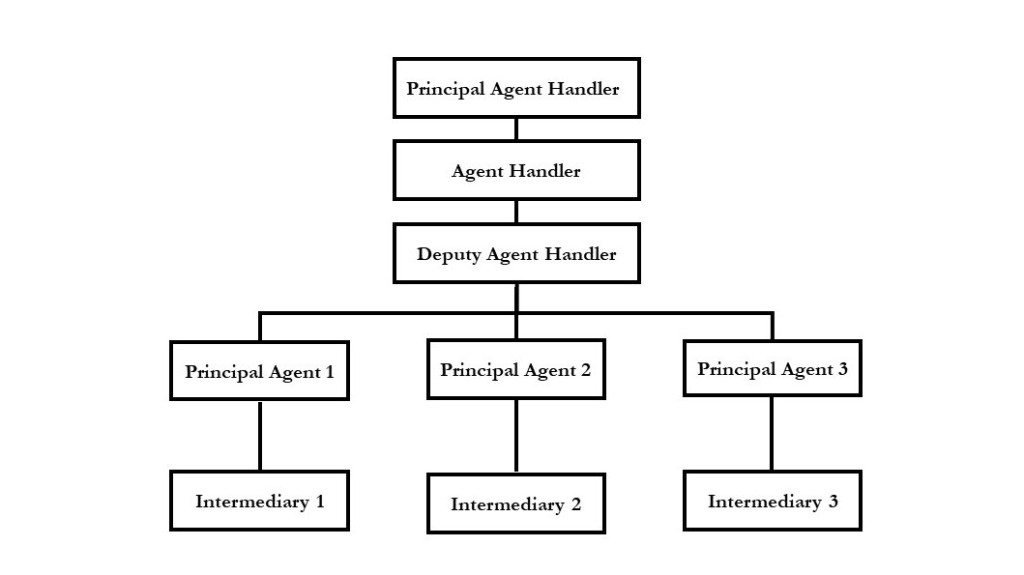
The PAH directed Agent Handler, Deputy Agent Handler, and Principal Agents within the organization’s controlled areas, who worked from inside offices and, therefore, were known as “Desk Agents.” There was another set of agents also directed by PAH who worked in the field (hostile area) controlled by the enemy and, therefore, were known as “Field Agents.” A middleman always worked as a “contact” or go-between Desk Agents and Field Agents, known as the Intermediary or Cut-Out.
In the hostile area, well-established agents working for the PAH, known as Resident Agents (RA), organized and directed compartmentalized “cells” operating there. Each Resident Agent dealt with a maximum of 4-5 Agents (A, B, C, D, and E) cultivated or hired and trained by those Desk Agents. As they worked under considerable risk, they were proactively given a cover story and a backstop to ensure their security. For instance, a well-known journalist living in a hostile area, sending and receiving information from all parts of the country, would have the perfect cover story to be a Resident Agent. A marine engineer working in a harbor would have an excellent cover story to be a source of information. See the diagram below for a visual representation of terrorist cells.

When a Resident Agent (RA) contacted one of his agents and/or informants to exchange information, he had to be extremely careful not to expose or compromise them to anyone, even to each other. He would meet with them in different Safe Houses. Afterward, the Intermediary would meet the Resident Agent in a separate Safe House and pass the information on further to the Desk Agents.
In exceptional cases, an Agent might contact the PAH directly without going through the Resident Agent and/or the Intermediary. The Agent would use covert communications and code sheets to pass the information in such instances. These kinds of cells were not only used to pass information but also to transfer other resources such as weapons and personnel.
For example, when LTTE’s Intelligence Wing planned an attack on Colombo Harbour, they began by acquiring a blueprint of the area. To achieve this, they identified a harbor employee by confirming his potential, mindset, motivation, and risk assessment, then hired him for the job of Agent/Informant. This Agent/Informant was instructed to contact the Resident Agent (RA) regularly and provide contemporary intelligence. An Intermediary would contact the Resident Agent to obtain the information to pass on to the Principal Agent or mail the data in segments directly to him.
They also hired another agent, such as an engineer at the harbor, to provide technical information such as storage, oil tanks, container terminals, warehouses, ammunition depots, etc. He offered the information to the Resident Agent. When traveling between the government-controlled area and LTTE’s controlled area, he gave the data directly to the Principal Agent or even the Principal Agent Handler, acting as an Intermediary himself.
Meanwhile, the Data Bank provided information to the Intelligence Wing for building a model of the harbor, and another cell was engaged to transfer weapons and personnel to the government-controlled area, using the same process of agent handling.
Finally, the attack squad was trained, briefed about the plan, and sent to the location using another route. Since this was an attack on a harbor, the assault team and weapons were moved to the location by a sea route.
For this mission, if a Black Tiger suicide bomber was required who had been cultivated as a “sleeper” to use long-term, he or she was also contacted by the Principal Agent Handler to brief the plan. He or she was provided weapons and resources through yet another cell. The Principal-Agent Handler did not, under any circumstance, expose or compromise the sleeper to the rest of the cells or vice versa to ensure everyone’s security.
Unlike “lone-wolf” terrorist attacks, the operations mentioned above would be coordinated terrorist attacks. That is to say, coordinated terrorist attacks are meticulously planned, painstakingly prepared, and professionally executed. It takes such clandestine components and social actors as sympathizers, logistic teams, intelligence teams, and bomb-making factories to facilitate coordinated terrorist attacks. See the diagram below for a visual representation of how compartmentalized terrorist cells and their members have become fragmented on the day of the actual terrorist attacks.

It is worth noting that since terrorist organizations learned their tactics from various nations’ state intelligence agencies once upon a time, the former also replicated the “Strategic Denial and Deception” military doctrine and various other intelligence tradecrafts. To illustrate, when terrorist organizations choose a primary target on the “Day of the Jackal,” they always attempt to deceive law enforcement agencies or the military by conducting a lower-scale attack elsewhere far enough and isolated from the actual target.
(6) Target Selection
When terrorists plan, prepare, and execute a target, they intentionally choose it soft or hard. A “soft target” is a person, thing, or location easily accessible to the public and relatively unprotected, making it vulnerable to terrorist attacks. By contrast, a “hard target” is heavily defended or inaccessible to the public. Examples of soft targets are shopping centers, sports arenas, and public transport, while hard targets can be embassies, military bases, navy destroyer ships, government buildings, etc. See the following diagram for a visual representation of the target selection of terrorists.

If terrorists select a hard target to attack, they provide exclusive training to the attack squad sufficiently in advance, based on the specific security surroundings of the target in question. For instance, when the LTTE Black Tiger suicide commandos carried out the raid on Anuradhapura Air Force Base, code-named Operation Ellaalan, on October 22, 2007, various Tiger specialists meticulously trained the attack squad. These military intelligence specialists are experts in reconnaissance, surveillance, explosives, landmines, heavy weapons, camouflage, etc. Hence, they train the attack squad according to the security settings of the target they have selected to attack based on the tactical and actionable intelligence in their possession. These trainers or specialists are called “Masters” in the LTTE, such as Thinesh Master, Sasikumar Master, Janan Master, Mathavan Master, Brindhan Master, Pradeep Master, Ratnam Master, etc. These masters are experts in specific skill sets listed below. See the following diagram to visualize the particular training terrorists provide for the suicide commandos (Black Tigers in the LTTE) while selecting hard targets.

Alternatively, when terrorists select a soft target to attack, they train the attack squad differently, depending on the target environment. Before the attack squad is assigned to a mission, they are instructed on every detail of the target. The target could be a football stadium or a World Trade Center – whatever it may be, the trainers brief every detail of the target as per real-time intelligence. The attack squad must learn about the specific physical environment to quickly identify selected targets. Keeping this in mind, many terrorist organizations sent their cadres to infiltrate hostile areas as disguised refugees, students, and government employees. Terrorists then choose them carefully after identifying and confirming their potential usefulness because they have already spent years within the target environment and have become a part of it. Their social and human capital is recognized as valuable human resources. See the following diagram to visualize the particular training terrorists provide for the suicide commandos (Black Tigers in the LTTE) while selecting soft targets.
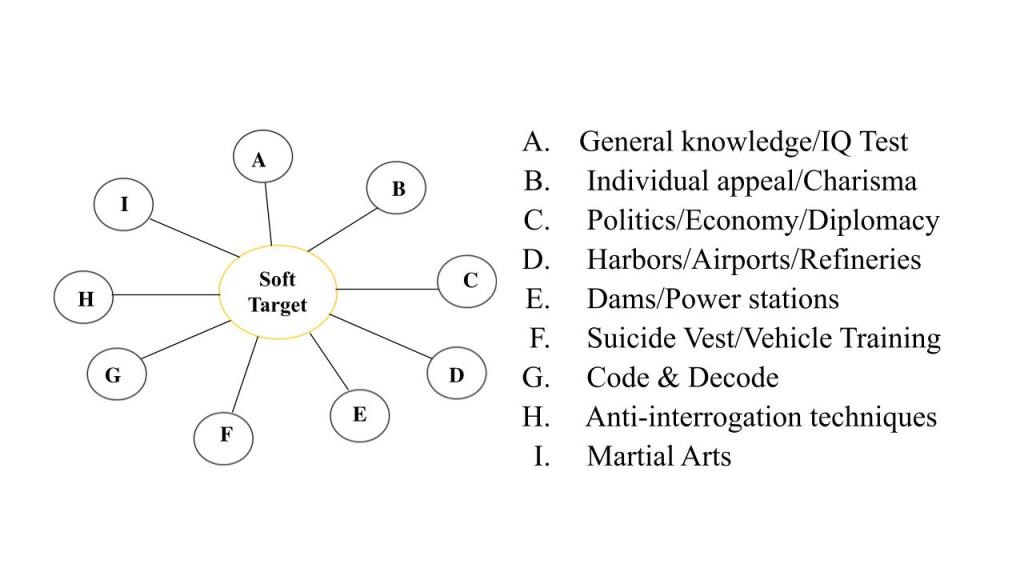
A good case in point is when the LTTE chalked out the strategy for conducting the raid on the World Trade Center in Colombo on October 15, 1997. First, they had sent a seven-member Black Tiger attack squad to infiltrate the southern and western provinces of Sri Lanka as sleeper agents. They were then proactively given a cover that they were students at the University of Peradeniya. These students also needed backstops: the names and addresses of safe houses that supported their legend. A legend is a sophisticated cover that amounts to a false life history and supporting documents to deceive law enforcement agencies or even established counterintelligence professionals. Before the LTTE had sent them to infiltrate and develop their cover stories, various Tiger specialists trained the attack squad according to the security settings of the target they had selected to attack. These trainers specialized in politics, economics, suicide vests, vehicle-borne improvised explosive devices (VBIED), heavy weapons, anti-interrogation techniques, etc. Before the attack, these students traveled between government-controlled areas and the LTTE-controlled areas to dry-run the chosen modus operandi and to rehearse the raid with their trainers many times.
Conclusion
According to Jane’s Sentinel Security Assessments, “…the LTTE was a highly innovative force capable of retaliation against aggression, reprisals, and pre-emptive strikes. Regular features of the LTTE doctrine included the unleashing of widespread terror on soft targets. Concentrating on lightly or unprotected targets is a classic diversionary tactic in warfare, pinning down troops to static sentry or bunker duties and restraining search and destruction operations. The LTTE had specialized in surprise raids – many of them suicide bombings. Prime ministers and presidents were killed, a high-security army, navy, and air force headquarters were infiltrated, passenger planes at the international airport were destroyed, and the country’s many economic infrastructures, including the Central Bank, were blown up. The LTTE bombed Sri Lankan passenger ships, commercial aircraft, trains, and buses; gunned down priests, nuns, pilgrims, and bystanders in a sacred royal city and shot Muslims while worshipping in mosques; frequently raided non-Tamil border villages and towns, massacring men, women, and children; and land mined, ambushed and assaulted military and police patrols and posts in Sri Lanka….”
Mao Zedong said that guerrillas are like fish in an ocean of people. The LTTE “fish” brilliantly exploited how to use the “ocean” of the general populace. Since every LTTE Intelligence Wing cadre was Sri Lankan of Tamil origin, the whole Tamil society in Sri Lanka came under suspicion. To detect and disrupt potential attacks, the Sri Lankan security forces established extreme security measures, including checkpoints, cordon and search operations, abductions, detention camps, aggressive interrogation, disappearances, harassment, and humiliation.
Tamil men and women are still being treated in this way daily because they could possibly be former LTTE Intelligence Wing cadres. These countermeasures of the Sri Lankan Security Forces, in turn, justify criticism that Tamils are not granted fundamental human rights within their own homeland.
-30-
Note: This is a living document. I am still researching; I will keep updating this document as I find more information on the subject. – Kagusthan Ariaratnam.
Featured images: TamilNet
Intelligence Terminology
– Agent: a person hired by an intelligence agency or security service to act in their interest.
– Backstop: support or backing information of an undercover operative to substantiate his/her cover story. It’s also known as Backup.
– Compartmentalization: management of an intelligence service so that information about the personnel, organization, or activities of one component is made available to any other part, only to the extent required for the performance of assigned duties.
– Cover Story: a persona, profession, purpose, activity, or fictitious image maintained by an agent or undercover operative.
– Dead-Letter Box (DLB): a physical location where communications, documents, and/or equipment are covertly placed for another person to collect without direct contact between the parties. It’s also known as a Dead Drop.
– Electronic Intelligence (ELINT): information derived by intercepting and studying electromagnetic radiation from non-communication sources, such as radar
– Human Intelligence (HUMINT): intelligence collected by humans.
– Imagery Intelligence (IMINT): an intelligence-gathering discipline that collects satellite and aerial photography information.
– Informant: a member of a target group who provides intelligence to the surveillance team or organization
– Intermediary: a contact or go-between used to preserve the safety or anonymity of the Principal and Resident Agents, also known as Cut-Out.
– Legend: a legend is a sophisticated cover that amounts to a false life history and supporting documents to deceive law enforcement agencies or even established counterintelligence professionals.
– Live-Letter Box (LLB): an address used to receive communication to be forwarded to an Agent and/or Intelligence Agency. It’s also known as a mail drop.
– Mole is a spy who works for an enemy nation whose loyalty lies within his nation’s government.
– Open Source Intelligence (OSINT): an information processing discipline that involves finding, selecting, and acquiring information from publicly available sources and analyzing it to produce actionable intelligence.
– Principal Agent: an agent who, under the direction of the principal-agent handler, is responsible for the operational activities of other agents.
– Resident Agent: the head of a legal or illegal residency in the hostile nation who supervises subordinate intelligence personnel.
– Safe House: a dwelling place or hideout unknown to the adversary.
– Signal Intelligence (SIGINT): intelligence-gathering by interception of signals, whether between people (i.e., COMINT or communications intelligence) or between machines (i.e., ELINT or electronic intelligence), or mixtures of the two.
– Sleeper: an inactive undercover agent who is cultivated for long-term use.
– Technical Intelligence (TECHINT): intelligence about weapons and equipment used by the armed forces of enemy nations, often referred to as foreign material.
– Tradecraft: specialized techniques used in intelligence operations.
Author Bio:
Kagusthan Ariaratnam is a defense analyst with over 25 years of experience who was formerly a child soldier of the Tamil Tigers. From 1990 to 2010, he worked with several international intelligence agencies in a substantial capacity. In 1992, Ariaratnam was appointed as an intelligence officer of the Tamil Tigers’ Military Intelligence Service. Between 1992 and 1995, he oversaw intelligence for the Sea Tigers and the Air Tigers, the organization’s rudimentary naval and air wings. Ariaratnam has unique knowledge of contemporary counterintelligence, counterinsurgency, and counterterrorism operations, as he has fought both as an insurgent during the Sri Lankan civil war with the Tamil Tigers and later against the insurgents as a military intelligence analyst with the Directorate of Military Intelligence of the Sri Lankan government. For his contribution to the “Global War on Terror,” Ariaratnam received the Institute of Defense and Strategic Studies Award in October 2003. He now studies digital journalism at the University of Ottawa and leads Project O Five Ltd. If you want to contact him, you can do so through email at kagusthan@gmail.com


I got to know this website from my pal who shared it with me, and thanks to him, I am browsing this weblog and reading very informative posts.
LikeLike
Hello there! I could have sworn I’ve been to this website before, but I realized it’s new to me after browsing through some of the posts. Nonetheless, I’m definitely delighted I found it, and I’ll be book-marking and checking back frequently!
LikeLike
Very good submit, I definitely love this website, keep on it
LikeLike
You have a great blog here! Would you like to make some invite posts on my blog?
LikeLike
I’m truly enjoying the design and layout of your blog. It’s very easy on the eyes which makes it much more pleasant for me to come here and visit more often. Did you hire out a developer to create your theme? Outstanding work!
LikeLike
Wow! This blog looks exactly like my old one! It’s on an entirely different subject, but it has pretty much the same page layout and design. Excellent choice of colors!
LikeLike
Lately, my colleagues and I have been deeply interested in the subject matter discussed on this forum. The information shared here is exceptional and has assisted me in my studies at least twice a week. This network has significant knowledge on this and other subjects, which is impressive. I do not usually browse websites when I am busy. Still, I keep myself updated with the latest information about my field of interest, especially when I have some free time.
LikeLike
It seems to be an excellent idea. I agree with you 100%.
LikeLike
Lately, my wife and I have been thinking about the information we need to help her and her kids in their studies twice a week or more. We found the information on this network to be very helpful and informative. This forum provides a lot of details, and it has been of great help to us. Although I am not always on the internet, I always search for this knowledge or other similar topics whenever I find the opportunity.
LikeLike
We are delighted to have discovered your website; it’s precisely what my friends and I have been searching for. The detailed information on the web page is without a doubt appreciated and is going to help me a bunch. It shows that everyone has a significant amount of specifics concerning the stuff I am interested in, and other pages and info likewise show it. Typically, I’m not on the net most of the time; however, when I have some time, I’m usually avidly hunting for this knowledge or others similarly related to it. I have a couple of my cohorts that have also developed a liking for this because of all that I have found out about it and they will probably be visiting this website since it’s such an incredible discovery. I’m also interested in politics and how to deal with the constant twists and turns in elections nowadays.
LikeLike
I started to feel that this website is like my close friend whom I am visiting every day and who helps me to grow in many senses.
LikeLike
Whoa, many of wonderful info!
LikeLike
Fantastic content. Cheers.
LikeLike
Pretty! This was an incredibly excellent article. Many thanks for providing this information.
LikeLike
After checking out a handful of the articles on your website, I like your technique of writing a blog. I added it to my bookmark website list and will be checking back shortly. Please visit my website as well and let me know your opinion.
LikeLike
Fantastic facts, Thanks a lot!
LikeLike
Hello, I used to read a piece of writing in newspapers but now I am a user of the web thus from now on I am using the net for posts, gracias!!!
LikeLike
Thanks a lot. Ample stuff!
LikeLike
You made your stand quite nicely!
LikeLike
Pretty! This has been an incredibly excellent article. Many thanks for providing these details.
LikeLike
Hello, a great topic for me. thanks, kelly
LikeLike
It is very interesting to find out, thank you.
LikeLike
I’m really enjoying the design and layout of your blog. It’s very easy on the eyes which makes it much more enjoyable for me to come here and visit more often. Did you hire a developer to create your theme? Outstanding work!
LikeLike
Hello, Neat post. There is a problem with your site in web explorer, might test this… IE nonetheless is the market leader and a large section of other folks will pass over your great writing due to this problem.
LikeLike
You made some decent points there. I did a search on the subject and found most persons will agree with your website.
LikeLike
Just wish to say your article is astounding. The clarity of your publication is just great and I suppose you are knowledgeable in this subject. Well along with your permission allow me to snatch your RSS feed to keep updated with upcoming posts. Thanks a million and please continue the rewarding work.
LikeLike